Open source tool leverages graphics processing to decrypt BitLocker-protected units
- Bitlocker Password Id
- How To Crack Bitlocker Password In Pendrive
- Breaking Bitlocker
- Lost Bitlocker Password
Matthew7560 Dec 5, 2018 at 4:45 AM. I ran into this issue if bitlocker was running while the system was doing updates or installing them after the download. Also, if the computer detects a hardware change after bitlocker has ran it can trigger this as well. Best bet would be to decrypt and run bitlocker again. Finding your lost BitLocker recovery key with John the Ripper Watch also: How to fix 'No OpenCL devices found' errorhttps://youtu.be/hTQD7fIzJBUCommands:Get.
Researchers have outlined their progress in further developing BitCracker, a GPU-powered password-cracking tool built specifically to break BitLocker, the full disk encryption built into Microsoft Windows.
A white paper (PDF) recently published by Elena Agostini, software engineer at Nvidia, and Massimo Bernaschi, director of technology at National Research Council of Italy (CNR), describes BitCracker as a solution designed to “attempt the decryption, by means of a dictionary attack, of memory units encrypted by BitLocker”.
BitCracker was first released in December 2015 and has been continually developed since.
Dictionary attack
BitLocker is Microsoft’s implementation of full-disk encryption, first released as an upgrade to Windows Vista in 2007. BitLocker is compatible with Trusted Platform Modules (TPMs) and encrypts data stored on disk to prevent unauthorized access in cases of device theft or software-based attacks.
BitLocker To Go works in the same manner for external devices, such as USB drives.
The technology uses 128 bit AES encryption by default, but this can be configured to 256 bits for a heightened level of security.

As BitLocker utilizes high levels of AES encryption, BitCracker relies on high-performance Graphics Processing Units (GPUs) to make a dictionary attack viable.
The software is available to the open source community and accessible via GitHub.

An OpenCL implementation of BitCracker was integrated with the popular, open source password hacking tool John The Ripper, version Bleeding-Jumbo, released last year.
“BitLocker decryption process requires the execution of a very large number of SHA-256 hashes and also AES, so we propose a very fast solution, highly tuned for Nvidia GPU, for both of them,” the researchers explain.
BitCracker has been tested with three Nvidia GPU architectures: Kepler, Maxwell, and Pascal.
LISTEN NOWSwigCast, Episode 2: ENCRYPTION
Bits and pieces
BitLocker uses two different modes of authentication; a user password or recovery mode, in which a user either types in a password to encrypt or decrypt a drive, or uses a 48-digit recovery key generated by BitLocker to access their content.
During encryption, each sector volume is encrypted individually using a Full-Volume Encryption Key (FVEK) and Volume Master Key (VMK), the latter of which is also encrypted and stored in the volume.
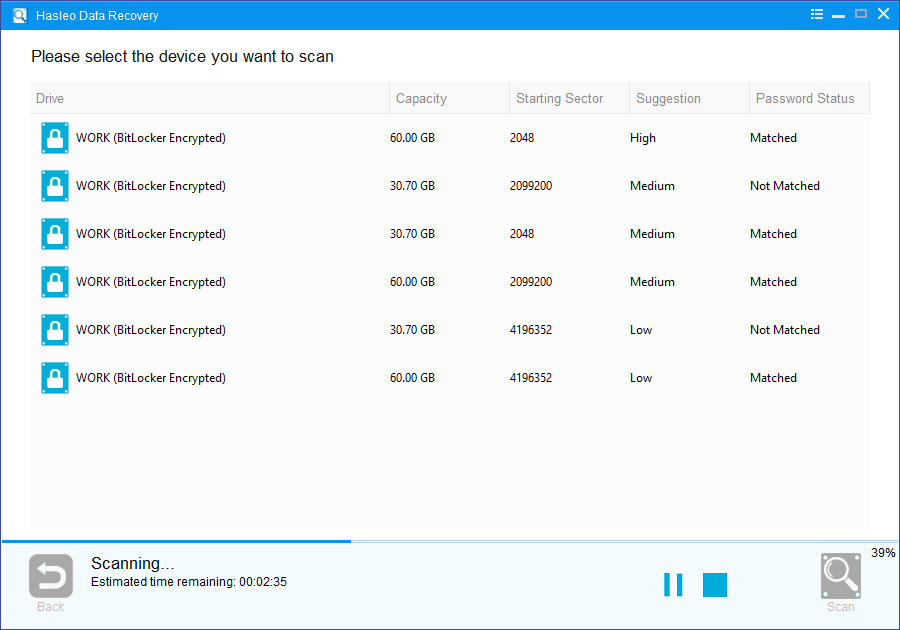
If a drive has been encrypted using the user password method, for example, in volume metadata you will find two encrypted VMKs – one encrypted with the user password and one encrypted with the recovery password.
During decryption, BitLocker begins decrypting the VMK, then FVEK, and then the disk itself.
Bitlocker Password Id
The BitCracker tool focuses on decrypting a VMK key, exposing a password capable of decrypting a device.
A dictionary attack is performed, leveraging GPU performance and power. The SHA-256 standard transforms messages into what is known as “W blocks” before being hashed, and so to speed things up, the team created a precomputation facility for some sets of W words, reducing the number of required arithmetic operations by creating a rainbow lookup table. This cannot be applied to other SHA-256 setups, however.
How To Crack Bitlocker Password In Pendrive
YOU MIGHT ALSO LIKEOpen source tools helps detect security of cloud containers

To further increase the speed of potential attacks, Agostini and Bernaschi were also able to remove MAC computation and comparison.
BitCracker’s performance was benchmarked against another popular password cracker, Hashcat, using a Pascal GPU.
The team acknowledges that the comparison is not entirely fair, as Hashcat does not use BitCracker’s W-block functions or MAC computation.
However, Hashcat was capable of 3,290 million hashes per second (MH/s), a result the researchers say is “comparable to BitCrackers’ best performance on the same GPU.”
BitLocker’s complex encryption process means that there is a limit to the number of passwords that can be tested at one time.
However, the research paper suggests that with a single high-end GPU, it is theoretically possible that over 122 million passwords could be attempted in only 24 hours.
“The results show that BitCracker may compete with a state-of-the-art password cracker in terms of raw performance on the basic computational kernels whilst it is the only one providing specific shortcuts to speed up the BitLocker decryption procedure,” the researchers explain.
Future developments
There are limitations to BitCracker. The tool is currently only able to evaluate passwords of between eight and 27 characters, and users must supply their own input dictionary.
In addition, BitLocker is often used in conjunction with a TPM in enterprise settings rather than relying solely on a user password, so attacks may be limited to consumer setups or perhaps individuals in particular organizations rather than company-wide deployments.
As noted by Reddit user and GitHub contributor Rarecoil, it is also the case that the tool is several years old, and both dictionaries and optimized rulesets have now advanced beyond BitCracker’s scope of attack.
Agostini and Bernaschi have also proposed methods to improve BitCracker in the future, including adding a mask mode attack or assigning smart probabilities to input dictionaries to speed up the process.
Microsoft declined to comment on the academics’ work.
Breaking Bitlocker
The Daily Swig has reached out to the authors of the paper but has not heard back at the time of publication.
Lost Bitlocker Password
READ MORESnufflepagus: Open source security tool hardens PHP sites against cyber-attacks