The STOP ransomware has seen very heavy distribution over the last month using adware installers disguised as cracks. This campaign continues with a new variant released over the past few days that appends the .rumba extension to the names of encrypted files.
Using adware bundles and software cracks as a new distribution method, STOP has become one of the most prolific ransomware infections we have seen in quite a while. First starting with the .djvu extension, then switching to the .tro extension, this latest .rumba variant continue to be heavily distributed as can be seen by the chart from ID Ransomware below.
Gandcrab is one of the most prevalent ransomware in 2018. October 2018, Gandcrab developers released 997 keys for victims that are located in Syria. Also, in July 2018, FBI released master decryption keys for versions 4-5.2. This version of decryptor utilises all these keys and can decrypt files for free. The.rumba ransomware virus is from the cryptovirus kind, meaning that it aims to encrypt the files on your computer in order to make them seem corrupt at least until you pay ransom to get them back. The ransomware then adds the.rumba file extension to the files of the computers encrypted by it and also drops the openme.txt ransom note. Memverifikasi apakah ransomware Rumba sudah sepenuhnya terhapus. Sekali lagi, penghapusan ransomware saja tidak mengarah pada dekripsi dari file pribadi Anda. Metode pegembalian data yang disorot di atas tersebut mungkin atau tidak mungkin melakukan trik, tapi ransomware sendiri bukanlah milik dalam komputer Anda.
A common practice used by sites that distribute software cracks is to utilize adware bundles in order to generate revenue. These bundles will normally install unwanted extensions, adware, clickers, and miners, but one bundler appears to be turning a blind eye and has started distributing the STOP Ransomware as well.
Can somebody please help me to decrypt.RUMBA files infected by DJVU ransomware? Attached is the file they copied in every folder.
Some of the reported cracks that are installing this ransomware include Windows activation cracks such as KMSPico, Cubase, Photoshop, antivirus software, and cracks for many other popular copyrighted software. From reports by infected users, it does not appear to be one particular crack site that is affected, but many different ones who are pushing similar adware bundles.
In this new variant, not much has changed and the developers continue to use the same approach as outlined in our DJVU article. The main difference is in this version the ransomware will append the .rumba extension to a file's name after it is encrypted as shown below.
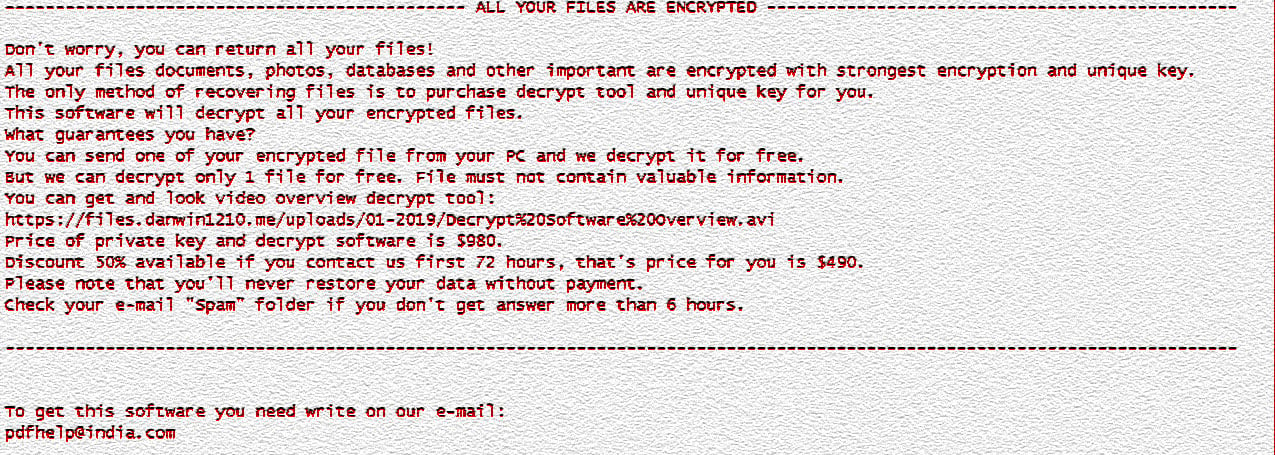
In each folder that a file is encrypted, the ransomware will create a ransom note named _openme.txt that contains instructions on how to contact the attacker for payment instructions.
The good news is that it may be possible to receive help in recovering your files for free. If you are infected with STOP Ransomware (.djvu, .tro, or .rumba), please see this post about using Michael Gillespie's decryptor.
If that fails to help, then please register an account and post the following information in a new reply to our dedicated STOP Ransomware Support & Help topic:
Rumba Ransomware Decryptor Error
- Network card's MAC address. This can be gotten from using the command getmac /v. If you are not sure which MAC address to use, feel free to copy the entire output.
- A link to two encrypted files. You can use the Wetransfer service for this.
- Your personal ID from the ransom note.
After you submit this information, we will try and help you, but please be patient..